
Antiphish Free Trial Request Form
We will answer your questions, discuss free trial details, then schedule employee training and testing.
By clicking «Submit» you agree to the personal data processing policy
Teaching Employees
to Protect Their Company against Cyberattacks
Antiphish is a platform to form skills to withstand all types of cyberattacks directed at people: via email, websites, social networks, messaging apps, etc.
Try 3 simulated attacks for free and receive a consultation about your company's security vulnerabilities
Key Customers
Most Cyberattacks Target Employees
A Q2 2020 report from Positive Technologies states that people are targeted in 59% of all attacks with social engineering (psychological manipulation) as a common attack method.
Modern attacks are based on psychology instead of technology
Attacks are disguised as daily communications (a letter from the management, a call from a bank, and so on), designed with psychological manipulations and intended for untrained employees.







Antiviruses, firewalls and spam filters do not provide full protection
Experts from Google, PayPal and Samsung have found that it takes at least 7 hours for an attack to be detected by technical means of protection.







Training courses are heavy on theory but forget about forming skills
To form information security skills you need real life practice. Only Antiphish designs and delivers targeted simulated attacks to train clients' skills in real life scenarios.







$170,000
According to Verizon's 2021 Data Breach Investigations Report (DBIR), phishing is the top «action variety» seen in breaches in the last year
The Antiphish Platform Forms Skills to Withstand Cyberattacks
The best defense for a company is employees that not only know the theory, but also have appropriate secure behavior skills.
Training course distribution and launching simulated attacks for employees is automated. All your security expert needs to do is check the scheduler's rules against your current security policy.
Our training has 3 stages

Every quarter employees spend less than an hour to study information security materials and then pass a knowledge verification test.
Training and Testing

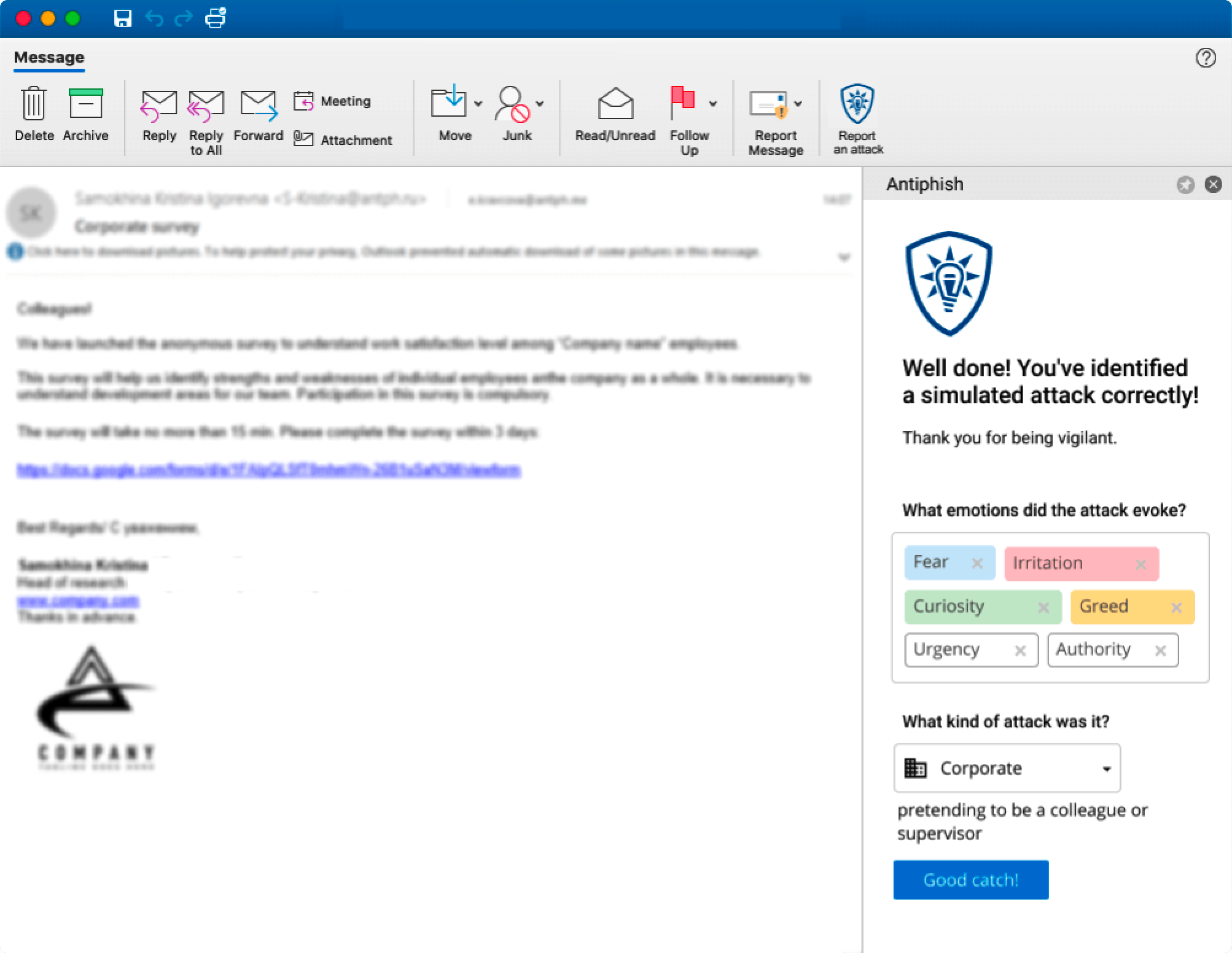
Every week every employee receives a simulated phishing attack to train and to verify their skills. The attack format depends on the skills that require development.
Skill Training

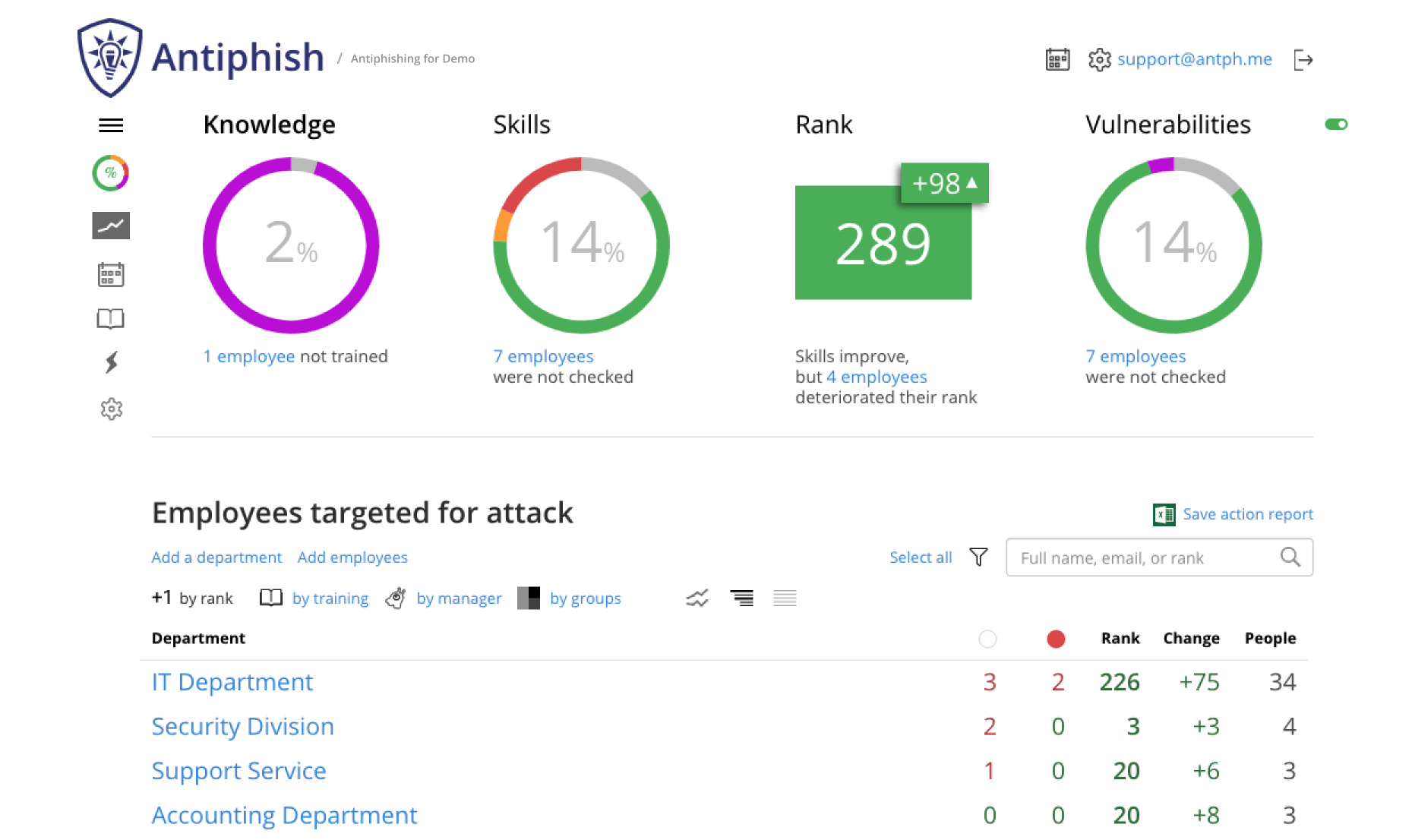
The platform calculates security ranks for employees, departments and the entire company based on actual skills. You will see an overall security rating that will allow you to prioritize your «more vulnerable» employees.
Results Evaluation
Try Antiphish for Free
Free 2-week trial to train 100 to 500 employees, perform simulated attacks and evaluate your overall security posture.
About Each Step
1. Training and Testing
2. Skill Training
3. Results Evaluation
During this stage employees are provided with essential InfoSec knowledge: types of cyberattacks, their general psychological mechanisms, and countermeasures.
Training covers all dangerous situations
Including attacks via email, websites, social networks, messaging apps, mobile devices, wi-fi networks, phone calls and removable media connected to a computer.
Up-to-date knowledge base with regular updates
We've been analyzing phishing and other cyberattacks against people since 2017. We know what knowledge and skills your employees need.
Natural learning environment
Our training curriculum contains examples of software your employees use: browsers, email, operating systems etc. No abstract or difficult to understand information.



Tests based on real life scenarios
Our tests simulate real life scenarios and gauge your employees behavior. Instead of just memorizing theory, we provide practical application.

During this step, secure behavior skills are developed through specially crafted simulated attacks targeted at your employees.
Training through obfuscated simulated attacks
Employees automatically receive emails, attachments, links to phishing sites, USB devices, and other content simulating a real attack.
We simulate 432 types of cyberattacks
Our proprietary classification covers the majority of cyberattacks against people. Employees learn to recognize and prevent different types of dangerous situations.
Instant feedback
Every simulated attack ends with feedback. We show employees what happened and explain how to act securely during a real situation.



We conduct OSINT and prepare customize attacks for our clients
We create new templates for targeted simulated attacks regularly, and make them more sophisticated than an actual malicious actor's version.

During this stage, the platform measures and improves the security performance of employees, departments and the entire company.
Knowledge level assessment
Which of the employees studied their courses (by topic) and their mandatory test pass rate. This metric reflects employees theoretic knowledge concerning cyberattacks.
Management reports
A visual representation on the effectiveness of the learning curriculum and skill development of your employees. Also includes a rank that shows the security posture of your employees, departments and the entire organization.
Skills and security posture assessment
Which employees prevent cyberattacks and which behave insecurely. This metric reflects employees practical development and your company's security posture.



Automated learning and training cycle
Employees that exhibit insecure behavior are automatically assigned additional courses and skill training through simulated attacks.

Fixing Vulnerabilities
Insecure behavior of employees during simulated attacks reveals software vulnerabilities in specific devices.This helps IT and InfoSec security teams identify and eliminate them.

Employees Skills after Using Antiphish
Employees will behave securely: recognize attacks and withstand them. And the company will not incur losses from malicious actors.
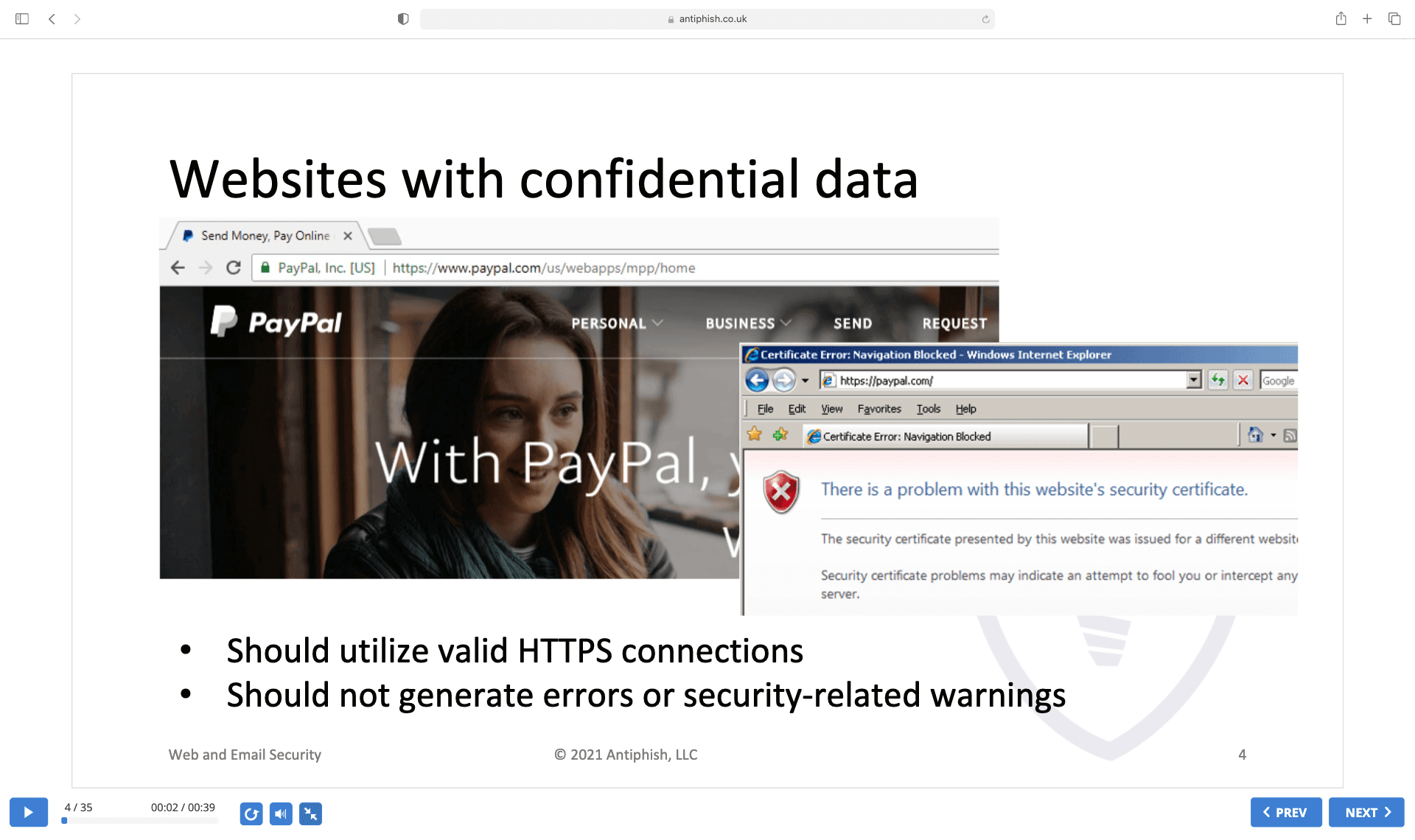
Websites
Email
Phone
Messaging Apps
Other Situations
Employee Protocol
1. Inputs the link address manually instead of clicking on a link from an unfamiliar email
2. Checks the HTTPS settings
3. Restricts access to the webcam and microphone on an unknown site
4. Informs the security team about errors or suspicious requests
Employee Protocol
1. Verifies the sender's address
2. Checks the link and attached documents
3. Checks the letter against psychological manipulations: fear, urgency, greed, etc
4. If the letter seems suspicious, reports it to the security team




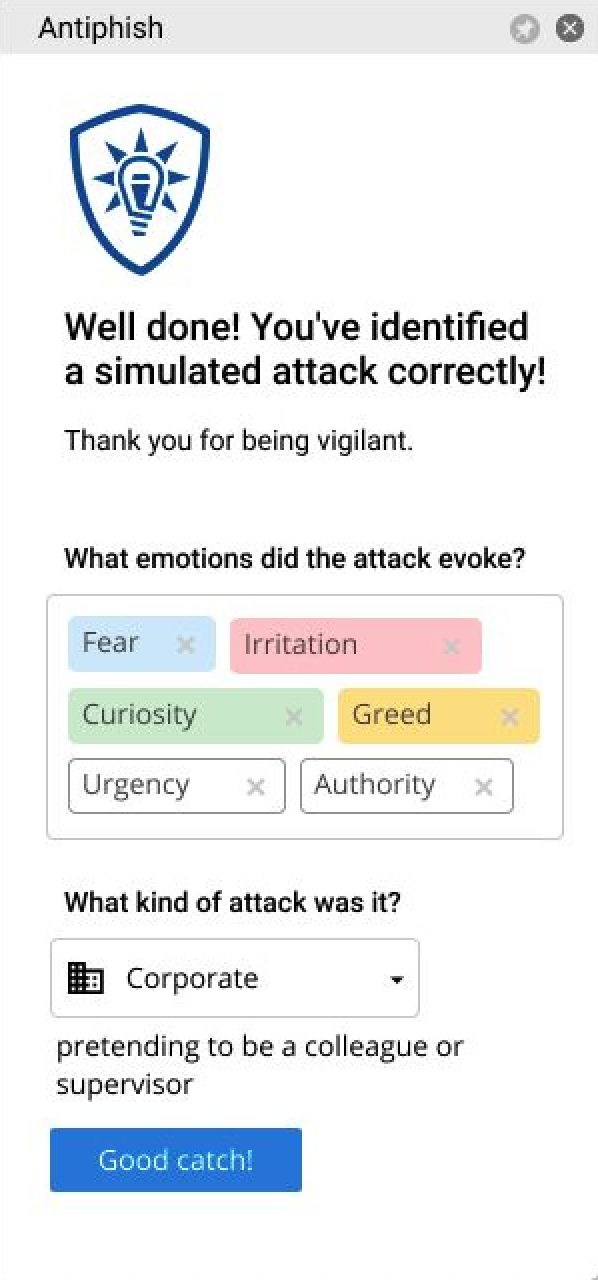
1. Verifies the sender's address
2. Checks the link and attached documents
3. Checks the letter against psychological manipulations: fear, urgency, greed, etc
4. If the letter seems suspicious, reports it to the security team
Employee Protocol
1. Avoids falling for emotions and manipulation: fear, urgency, authority
2. Hangs up, even if it's the «Law Enforcement Officer» calling
3. Calls back to the bank or the company/department the call came from
Listen to an employee of an unscrupulous debt collector trick a victim into paying by pretending to be a law enforcement officer and illegally threatening arrest and other legal action.

Employee Protocol
1. Carefully checks details of the offer (in this case, the working hours and accommodation are not what the au pair program usually offers)
2. Verifies the email address of a prospective employer
3. Ignores demand to send any fee at very short notice
Recognizes emotions the scammers are trying to evoke
Reports the attack to the security department


The Advantages of Using Our Platform
By understanding the security processes of large companies, we created a product that that suits even the most demanding of clients.
Integrating into Security Processes
Antiphish provides an open API. Thus you can configure integration with any internal and external systems in your company — LMS, LDAP, SGRC, IRP, SIEM, IDM etc.



Automated Learning and Training Process
Learning, skill training, vulnerability detection and reporting are all automated. Admins do not waste time on routine tasks due to the scheduler and Antiphish API.



Unlimited Scaling
The platform can be integrated into a geographically distributed infrastructure and scaled for ten to a hundred thousand employees.



Constant Customization
Training courses and attack templates are custom built with regard to your company's information security policies and actual threats.



How many of your employees behave insecurely?
Try Antiphish platform for free to find out.











